When deciding which Bitcoin brokerage to do business with, and to potentially store funds with, it is important to understand the custody model that an organization employs. Is the firm leveraging potentially exploitable, proprietary technology? Or are they utilizing Bitcoin’s native, open-source multisig technology to secure funds?
River is a technology company at its core, and we pride ourselves on our customer-centric, conservative approach to all aspects of our business. We’re committed to providing operational transparency to our clients—especially when it comes to securing funds. All bitcoin stored on our platform is backed 1:1, clients completely own their account balance.
This is a follow-up to our article How Your Bitcoin Flows Through River from earlier this year. We’ll cover how we think about creating secure custody for our clients: what client funds are safe from, and how we keep them safe.
Security In Layers of Redundancy
What do we mean by redundancy? In an engineering context, redundancy means that critical aspects or functions of a system are duplicated—typically in the form of a backup—in order to remove single points of failure. In the context of our custody solutions, this means creating and safeguarding the private keys that secure the bitcoin.
River’s custody solutions are implemented such that each piece of the puzzle has backup options—keys for the vault are generated in separate locations, and each key has several digital backups, as well as multiple physical backups. The backups are then stored in different physical locations.
Geographically distributing backups is a form of geo-redundancy: these practices work to mitigate unforeseen, external events that are rare. Consider a scenario where the keys for a multisig vault are all generated and stored in the same location; if there is a natural disaster or a fire, the keys could be gone, and funds might be lost.
If the keys for the vault in the above scenario were physically backed up—non-digital media—then funds would still be secure even if all electronic systems failed. Our cold storage is designed such that, even if unexpected events happen in multiple locations across the U.S., client funds would be secure.
No Single Points Of Failure
River’s cold storage vault leverages Bitcoin’s multisig scripting capabilities; this is important because it means the basis of our custody solution has effectively had several hundred code reviews from open-source Bitcoin contributors. And because Bitcoin’s multisig technology is open-source, we are able to build upon this resource while maintaining privacy for our internal systems.
As indicated in the previous section, geo-redundancy measures are taken to ensure that private keys associated with the vault are generated and secured in separate geographic locations.
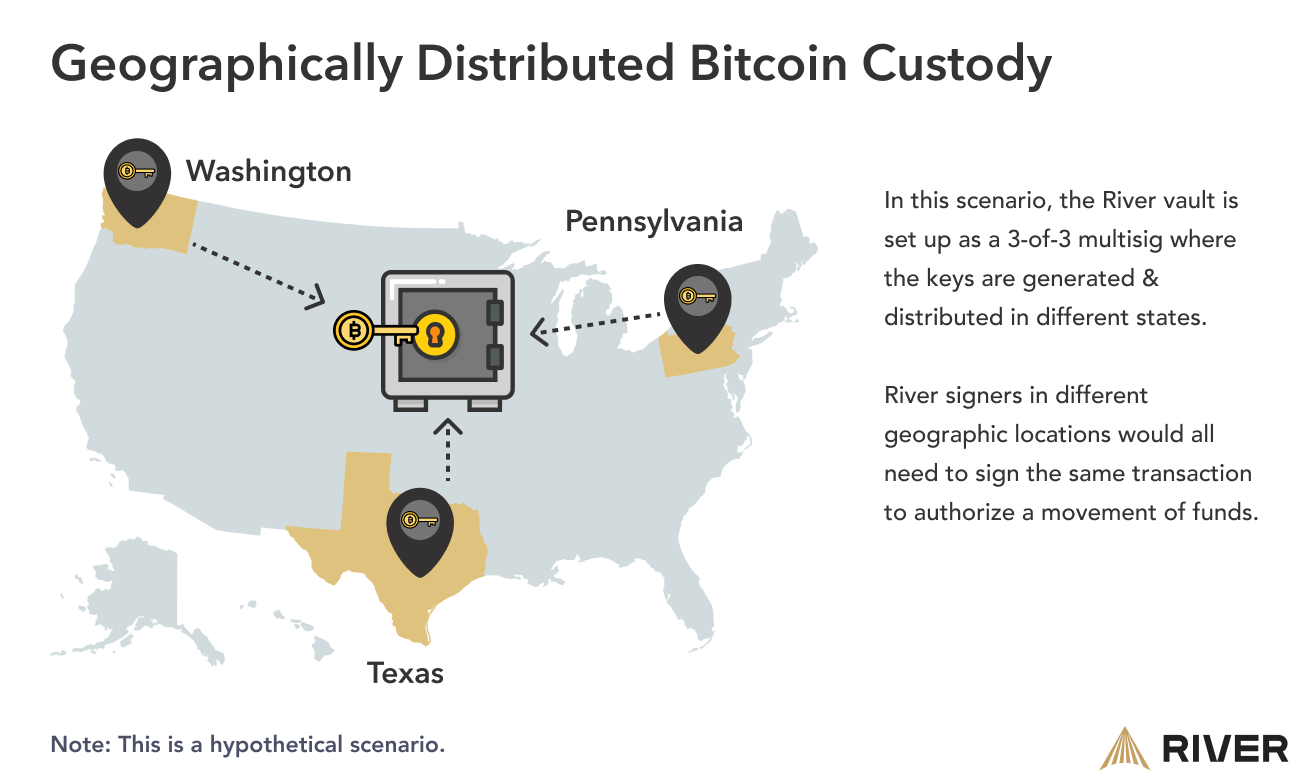
In a hypothetical scenario, a River cold storage vault might be set up as a 3-of-3 multisig with keys generated in Washington, Texas, and Pennsylvania and physically durable copies of keys stored separately for redundancy.
Furthermore, there are no single points of failure for fund movements. In order to successfully withdraw bitcoin from the vault, multiple, geographically distributed signers must sign off on the transaction.
Our cold storage vault is purpose-built to ensure that there are no single points of failure throughout our security model; our solutions are constructed to ensure our clients’ funds remain secure in even the most unlikely scenarios.
Wallets for Daily Movements
Our cold storage solution is highly secure, but it is not convenient for day-to-day business operations. We need to move funds for things like client withdrawals, settling trades with our OTC counterparties, and treasury management. Therefore, we utilize a hot wallet system for our operational needs. Note that hot wallets rarely ever secure more than 2-5% of funds on the platform.
We have systems in place to mitigate the risks of operating hot wallets. Multiple approvals are required to process transactions even though only a small fraction of client funds are kept online. As a result, a hacker could compromise a device with extensive system permissions, and still come up empty-handed.
The Devil’s in the Dependencies
When entrusting a third party with your funds, it’s important to understand that any components within the custody solution that rely on external inputs are potential attack vectors. In software development, reliance on external support is called a dependency. While it’s not wrong to leverage other developers’ work, it does mean that whatever product or service you are building literally depends on another piece of software to function properly.
Reliance on third-party service providers is also a form of dependency. Simply put: if your bitcoin custody provider has not built their own cold storage vaults, there is a chance that they do not have insight into the quality of their security systems
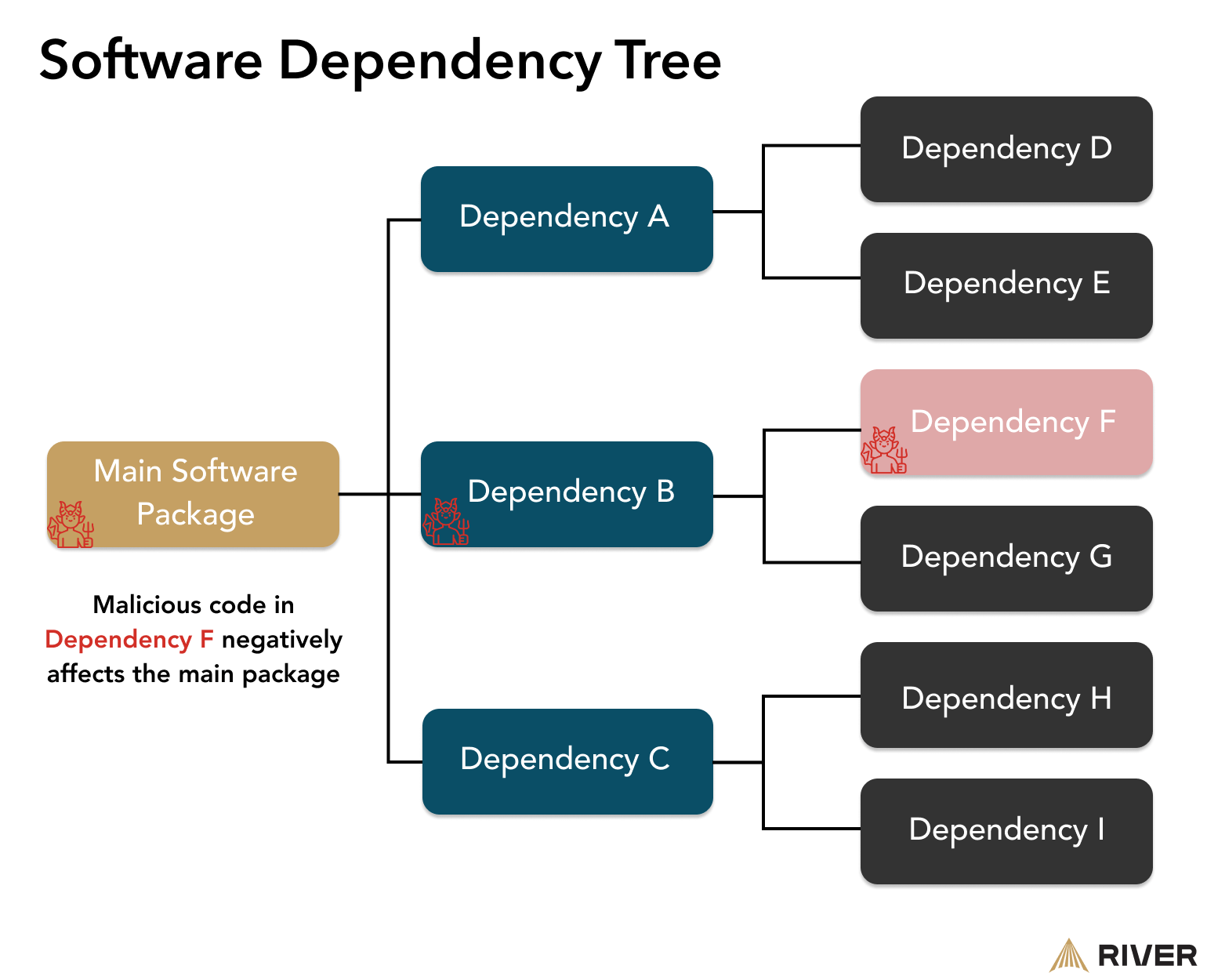
At River, we prioritize building as much of our own infrastructure as possible in order to minimize external dependencies. Our brokerage platform, Lightning infrastructure, wallet software, cold storage vaults, and River Learn platform were all developed from scratch and are maintained in-house. We are comfortable with a slightly longer development process because we can ensure a higher degree of security assurance for our clients.
Security Is Downstream From Culture
Our culture at River empowers each employee to take ownership of all the projects that we work on. A responsibility that we all share and take seriously is protecting our clients’ funds and data. Good client experiences start with the understanding that if you choose to custody funds on our platform, we ensure their safekeeping.
Any changes made to our code base must pass through at least two separate code reviews, as a means of ensuring that client experiences are not negatively impacted. Along similar lines, access to different kinds of data is permissioned based upon an employee’s role—if we don’t need access to effectively do our job, then we will not have access. Employees who have access to sensitive information are further supported by highly skilled data security, legal, and compliance professionals.
Conclusion
River was founded on the idea that building infrastructure from scratch, minimizing external code dependencies, and focusing on security create a sturdy foundation for a Bitcoin business to best serve clients.
All bitcoin on River is backed 1:1 and 98% is stored in a multisig vault where keys (and their backups) are geographically distributed. Our custody solution was designed with edge cases in mind; even in the (unlikely) event of severe natural disasters, fires, and sophisticated hacking attempts, client funds remain safe.
We take a conservative approach to the products and services we market to current and prospective clients. Security is always top of mind for us during and after product development.
Our primary business is not as a bitcoin custodian—we actively encourage self-custody—but we believe it is important to provide a top-quality solution for those not yet ready to practice self-custody. Transparency is central to our ethos: building our own infrastructure means a longer development process, but the end result is sleep-at-night technology and satisfied clients.
If you're ready to partner with a platform that helps you sleep at night knowing your Bitcoin is safe, get started by downloading our iOS app or signing up at River.com. If you have any questions along the way, please feel free to reach out to our Support Team who will be happy to assist you on your Bitcoin journey!

